Mastering Identity Propagation in Agentic Systems: Strategies and Challenges

- Authors
- Published on
- Published on
In this riveting episode by IBM Technology, they delve into the thrilling world of identity propagation in agentic systems. They tackle the challenges head-on, exploring various delegation patterns like trusted assertion and simple delegation. The team introduces the concept of on behalf of delegation, where agents work on behalf of users, adding a layer of complexity to the already intricate system. They also shed light on the intriguing idea of multiple identity providers across organizational boundaries, a concept as daring as it is essential in today's interconnected world.
To combat these challenges, the experts propose a series of ingenious strategies. They advocate for the use of OAuth 2 and OIDC as industry standards to ensure seamless communication between different entities. The concept of token exchange at each node along the agentic flow emerges as a crucial mechanism to validate user identities and maintain the integrity of the system. Leveraging context, scope, and audience becomes paramount in narrowing down user access rights and preventing unauthorized actions, a strategy as clever as it is effective.
Furthermore, the team emphasizes the importance of connecting nodes via APIs and utilizing API gateways to streamline the token exchange process. By centralizing this operation, they not only simplify the workflow for developers but also enhance the overall security of the system. Lastly, the experts stress the significance of continuous monitoring to ensure compliance and security across the agentic flow. IBM Technology's insightful exploration of identity propagation in agentic systems offers a glimpse into the future of secure and efficient data management in the digital age.

Image copyright Youtube
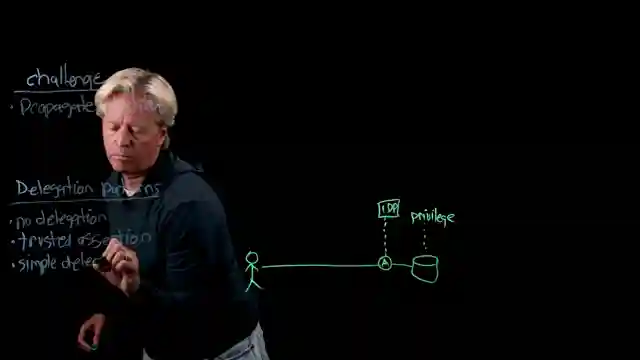
Image copyright Youtube
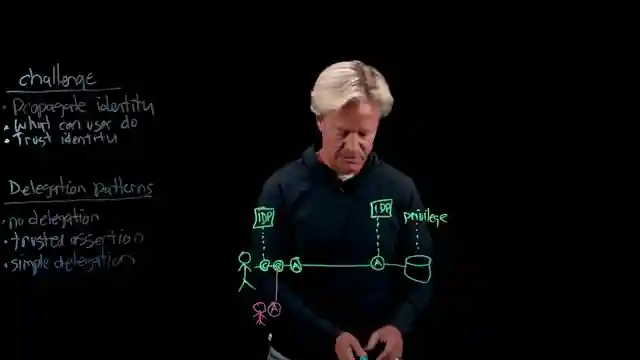
Image copyright Youtube
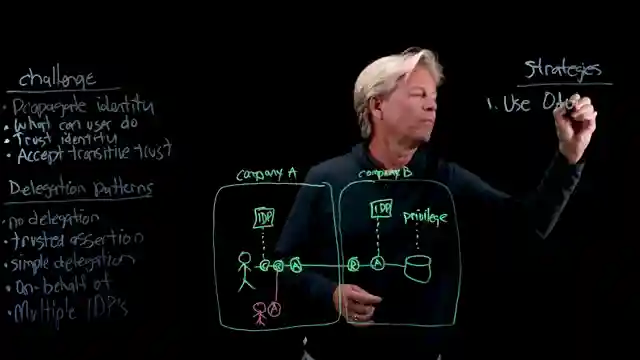
Image copyright Youtube
Watch How will AI Agents Manage Identity & Build Trust in Complex Systems on Youtube
Viewer Reactions for How will AI Agents Manage Identity & Build Trust in Complex Systems
Positive feedback on the exploration of identity propagation challenges within agentic systems
Mention of delegation patterns discussed in the video
Highlight on the potential of verifiable credentials (VCs) and decentralized identifiers (DIDs) in reinforcing cross-boundary trust
Mention of enhancing identity assurance in dynamic, multi-organizational agentic flows with VCs and DIDs
Appreciation for the contribution to the future of trusted AI
Mention of potential PAM strategies like ZSP in agentic workflows
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
