Mastering AI Security: The Donut of Defense Approach

- Authors
- Published on
- Published on
In this riveting IBM Technology episode, the team delves into the thrilling world of AI security, likening it to a tantalizing "donut of defense". They emphasize the critical need to fortify AI by safeguarding its data, model, usage, infrastructure, and governance layer. Introducing a groundbreaking donut diagram, they ingeniously propose a comprehensive approach to unite these essential defenses for maximum protection. From discovering all AI implementations, including shadow AI, to meticulously assessing vulnerabilities and conducting rigorous pen testing on AI models, the team leaves no stone unturned in ensuring a rock-solid security posture.
Furthermore, the team highlights the importance of control measures, such as implementing an AI gateway to thwart prompt injection attacks and safeguard against privacy breaches. By establishing guardrails to prevent unauthorized actions and monitoring for potential threats, they demonstrate a proactive stance in fortifying AI defenses. The emphasis on compliance with regulations and security policies underscores the team's commitment to upholding the highest standards of data protection and integrity. Through meticulous risk management and visualization of prioritized risks via a comprehensive dashboard, the team empowers viewers to make informed decisions and stay ahead of potential security threats.
In conclusion, the team's strategic approach of discover, assess, control, and report culminates in a robust defensive strategy that promises to render AI impervious to breaches. By meticulously integrating these key security measures, viewers are equipped with the knowledge and tools needed to navigate the complex landscape of AI security with confidence and resilience. IBM Technology's insightful exploration of AI security not only educates but also inspires viewers to embrace the challenge of safeguarding AI in an ever-evolving technological landscape.

Image copyright Youtube

Image copyright Youtube
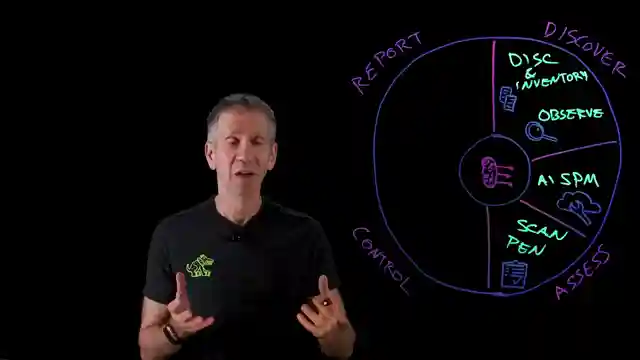
Image copyright Youtube
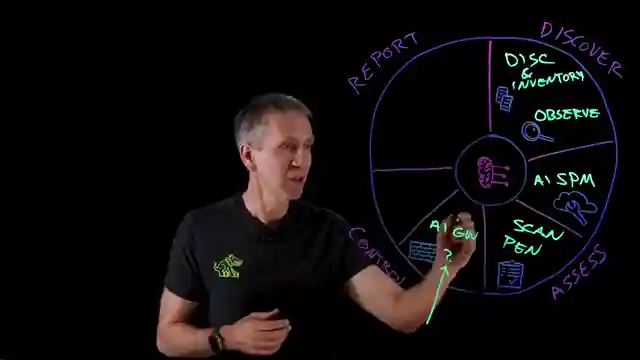
Image copyright Youtube
Watch Securing AI Systems: Protecting Data, Models, & Usage on Youtube
Viewer Reactions for Securing AI Systems: Protecting Data, Models, & Usage
Importance of understanding the donut paradigm
New perspective on security in GenAI
Data security posture management
Appreciation for the teaching style
Request for technical paper on AI Security model
Personal experiences related to the subject
Concerns about AI potentially deceiving in the discovery phase
Emphasis on engineering challenges over legal issues
Request for video on starting a career in Gen AI
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
