Evolution of Identity Governance: Navigating the World of Agentic Systems

- Authors
- Published on
- Published on
In this riveting IBM Technology video, we embark on a thrilling journey through the evolution of identity governance, from the ancient days of the 1960s to the cutting-edge era of agentic systems. Picture this: people storing files on mainframes, pondering questions like "Who am I?" and "What am I trying to store?" Fast forward to the '70s and '80s, where databases and applications sprouted like mushrooms after rain, flooding the network with data, systems, and users. The need to provision users, authenticate them, and manage their access became paramount in this digital jungle.
But hold on to your seats, because the real excitement begins with the emergence of agents within our systems. These agents, dynamic entities with complex handoffs and interactions, are revolutionizing the game. Unlike our traditional deterministic process flows, these agents operate in a dynamic, unstructured manner, navigating through intricate webs of data and systems. Their adaptability allows them to make on-the-fly decisions, autonomously choosing their path within defined parameters. It's a high-stakes game of governance to ensure these agents don't go all "HAL 9000" on us.
To govern these enigmatic agents effectively, a strategic approach is crucial. From establishing unique identities to implementing context-aware and ephemeral access controls, every move counts in this high-octane world of agentic systems. Segmentation and isolation play a key role in limiting an agent's scope of operation, reducing the risk of a catastrophic breach. Observability is the final piece of the puzzle, providing transparency into the actions of these agents and keeping us audit-ready at all times. Buckle up, folks, because the future of identity governance is here, and it's a wild ride into the unknown.

Image copyright Youtube
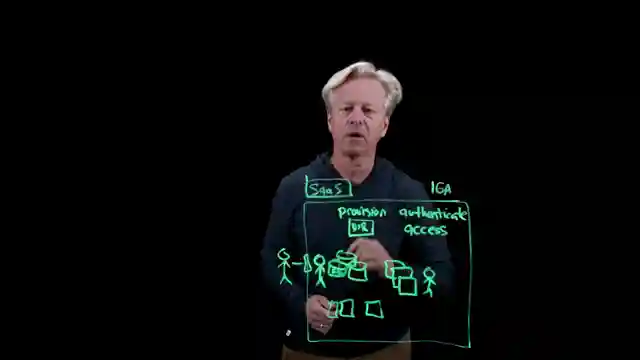
Image copyright Youtube
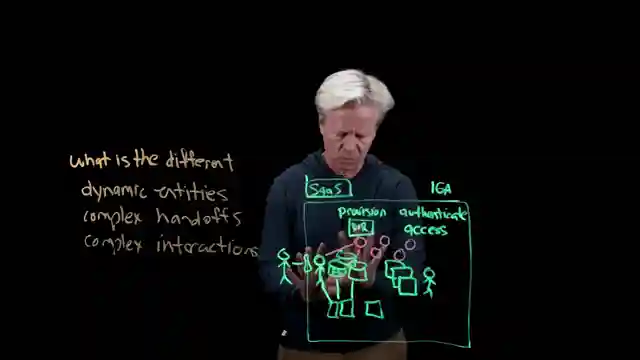
Image copyright Youtube

Image copyright Youtube
Watch What Are AI Identities? Understanding Agentic Systems & Governance on Youtube
Viewer Reactions for What Are AI Identities? Understanding Agentic Systems & Governance
IBM's AI technology is impressive
Positive feedback on IBM's advancements in AI
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
