Enhancing Cybersecurity: Preventing Password Hacks and Protecting Digital Assets

- Authors
- Published on
- Published on
In this riveting IBM Technology episode, we delve into the dark world of cybercrime where villains employ cunning tactics to crack passwords and infiltrate systems. From the art of guessing to the insidious act of harvesting, these hackers stop at nothing to gain unauthorized access. Picture this: a malevolent figure using keyloggers to steal passwords or attempting to reverse hashed passwords through cracking techniques. It's a high-stakes game of cat and mouse, with attackers utilizing spraying and stuffing methods to breach multiple accounts or systems.
To combat these cyber threats, IBM recommends a multi-faceted approach. Strengthening password complexity, leveraging password managers, and implementing multi-factor authentication are just a few strategies to fortify your digital defenses. The key takeaway? Length is strength when it comes to passwords, and using unique passwords across different platforms is crucial. Additionally, embracing passkeys and employing rate limiting can significantly bolster your cybersecurity posture.
When it comes to detection, vigilance is key. Monitoring for multiple login failures over time or across various accounts can help flag potential attacks early on. And in the event of a breach, a swift response is paramount. Blocking suspicious IPs, disabling compromised accounts, and enforcing password changes are essential steps to thwart cyber adversaries and safeguard your digital assets. By staying proactive and vigilant, you can outsmart the hackers and ensure your online security remains intact.

Image copyright Youtube

Image copyright Youtube

Image copyright Youtube
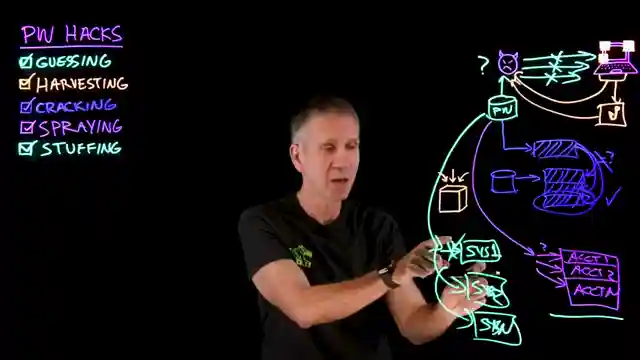
Image copyright Youtube
Watch How Hackers Steal Passwords: 5 Attack Methods Explained on Youtube
Viewer Reactions for How Hackers Steal Passwords: 5 Attack Methods Explained
Positive feedback on the team's work
Blessings for the team
Appreciation for the content quality
Related Articles

Mastering Identity Propagation in Agentic Systems: Strategies and Challenges
IBM Technology explores challenges in identity propagation within agentic systems. They discuss delegation patterns and strategies like OAuth 2, token exchange, and API gateways for secure data management.

AI vs. Human Thinking: Cognition Comparison by IBM Technology
IBM Technology explores the differences between artificial intelligence and human thinking in learning, processing, memory, reasoning, error tendencies, and embodiment. The comparison highlights unique approaches and challenges in cognition.

AI Job Impact Debate & Market Response: IBM Tech Analysis
Discover the debate on AI's impact on jobs in the latest IBM Technology episode. Experts discuss the potential for job transformation and the importance of AI literacy. The team also analyzes the market response to the Scale AI-Meta deal, prompting tech giants to rethink data strategies.

Enhancing Data Security in Enterprises: Strategies for Protecting Merged Data
IBM Technology explores data utilization in enterprises, focusing on business intelligence and AI. Strategies like data virtualization and birthright access are discussed to protect merged data, ensuring secure and efficient data access environments.
