Malleable and Homomorphic Encryption: Securing Data in a Digital World

- Authors
- Published on
- Published on
Today, Tim takes us on a thrilling journey into the treacherous world of malleable encryption. It's like giving a burglar the keys to your house - anyone, even attackers, can tamper with your encrypted data. Using examples like the vulnerable one-time pad, Tim shows how perfect encryption can be twisted and exploited by cunning adversaries. It's a bit like leaving your front door wide open for anyone to stroll in and help themselves to your valuables.
But fear not, because Tim also introduces us to the intriguing concept of homomorphic encryption, exemplified by the renowned RSA system. This technology allows for mathematical operations on encrypted data without the need for decryption, opening up a world of possibilities. However, as Tim demonstrates, even this powerful encryption method is not immune to the devious tactics of attackers who can manipulate values to their advantage. It's like having a state-of-the-art security system that can still be outsmarted by a crafty thief.
Furthermore, Tim delves into multiplicative homomorphic encryption, where the lines between multiplication and addition blur in the encrypted realm. By showcasing how operations on ciphertexts can impact plaintext, he unveils the fascinating world of homomorphic properties. From manipulating vote tallies without compromising individual votes to exploring the limitations of deterministic encryption in RSA, Tim navigates the complex landscape of secure data transmission with precision and flair. It's a high-octane ride through the intricate maze of encryption technology, where every move counts and every vulnerability is a potential pitfall.

Image copyright Youtube
Image copyright Youtube
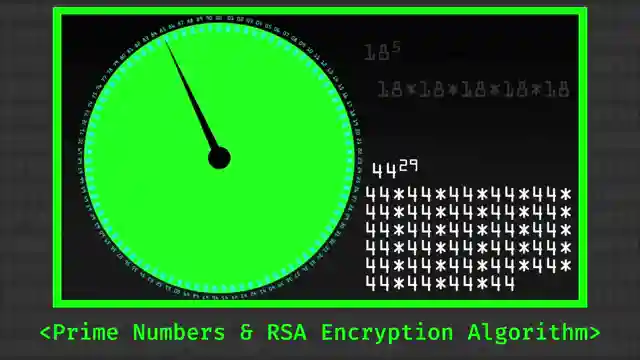
Image copyright Youtube

Image copyright Youtube
Watch Malleable Encryption - Computerphile on Youtube
Viewer Reactions for Malleable Encryption - Computerphile
Suggestion to add high pitch server room noise for authenticity
One-time pad stipulations: key length, randomness
Request for a working marker instead of repurposed whiteboard marker
Positive feedback on the explanation video
Suggestion to add random wasted space to prevent bit flipping
Difficulty in following the video for someone with little prior knowledge of one-time pads
Request for a video on Schnorr signatures
Homemade one-time-pad app encryption method using leading bits for rearrangement
Confusion about "P crypto system" mentioned in subtitles
Question about workaround for authority knowing who voted what in an unbiased voting system
Related Articles

Unleashing Super Intelligence: The Acceleration of AI Automation
Join Computerphile in exploring the race towards super intelligence by OpenAI and Enthropic. Discover the potential for AI automation to revolutionize research processes, leading to a 200-fold increase in speed. The future of AI is fast approaching - buckle up for the ride!

Mastering CPU Communication: Interrupts and Operating Systems
Discover how the CPU communicates with external devices like keyboards and floppy disks, exploring the concept of interrupts and the role of operating systems in managing these interactions. Learn about efficient data exchange mechanisms and the impact on user experience in this insightful Computerphile video.
Mastering Decision-Making: Monte Carlo & Tree Algorithms in Robotics
Explore decision-making in uncertain environments with Monte Carlo research and tree search algorithms. Learn how sample-based methods revolutionize real-world applications, enhancing efficiency and adaptability in robotics and AI.
Exploring AI Video Creation: AI Mike Pound in Diverse Scenarios
Computerphile pioneers AI video creation using open-source tools like Flux and T5 TTS to generate lifelike content featuring AI Mike Pound. The team showcases the potential and limitations of AI technology in content creation, raising ethical considerations. Explore the AI-generated images and videos of Mike Pound in various scenarios.
